July 24th, 2018 | By Administrator
There was a major breach at Tim Hortons location that affected almost 1000 stores as the virus damaged the cash registers. The POS system (POS) of over 160 Applebee’s restaurants were infected with malware to gain access to the customers’ names, bank card details, verificati...
MORE
June 28th, 2018 | By Administrator
A Point of Sale (POS) system is an easy to use and efficient option for processing transactions in a shop or restaurant. POS systems are capable of generating sales reports and stock inventory instantly which make it easier to manage the business. POS systems have been desig...
MORE
June 14th, 2018 | By Administrator
In today’s increasingly connected and digital business environment, the incidence of zero-day attacks and consequences of data breaches are on the rise. Many well-known companies all over the world today have suffered from data breaches and zero-day attacks that have c...
MORE
June 1st, 2018 | By Administrator
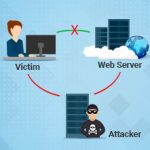
A zero-day attack exploits a security vulnerability in computer software or hardware, even before a specific preventive measure or patch exists for that vulnerability. Zero-day attacks come from criminal hackers who have taken advantage of a previously unknown vulnerability...
MORE
May 11th, 2018 | By Administrator
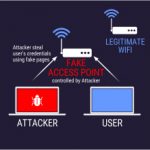
Cyber criminals find new ways, methods, and techniques to attack a user’s device or to even attack an organization’s network. One such type of attack is called Man in the Middle Attack. In this article, let’s discuss the Man-in-the-Middle Attacks. What is Man-In-The-Mi...
MORE
May 10th, 2018 | By Administrator
Cybercrime has evolved from individuals who commit online fraud for their personal profit into a sophisticated and networked criminal industry… With a rise in new forms of sophisticated malware threats, protecting online data has become a serious concern. The current s...
MORE
April 21st, 2018 | By Administrator
In recent times, there has been a sudden spike in the number and sophistication of cyber attacks globally. Due to this, cybersecurity experts have adopted various new technologies to combat Trojans, Ransomware, and other types of Malware. Infamous ransomware attacks like the...
MORE
April 19th, 2018 | By Administrator
Be it a small retail shop or large shopping center; no business is complete without a POS (Point of Sale system). In today’s world of technological innovations, the sky is the limit as to what your business can achieve. Regardless of your business vertical, Point of Sa...
MORE
April 14th, 2018 | By Administrator
Zero-day attacks take advantage of a previously unknown vulnerability in an application or Web service that has not been addressed or patched by the creators of that application or Web service. Since the zero-day vulnerability is previously not known, the zero-day exploits o...
MORE
April 13th, 2018 | By Administrator
What is man-in-the-middle attack? As the name suggests, the man-in-the-middle attack is staged by a malicious user who secretly inserts him/herself between two communicating parties. So, when a hacker intercepts two unsuspecting parties he/she monitors the entire conversatio...
MORE