Cyber criminals find new ways, methods, and techniques to attack a user’s device or to even attack an organization’s network. One such type of attack is called Man in the Middle Attack. In this article, let’s discuss the Man-in-the-Middle Attacks.
What is Man-In-The-Middle-Attack?
A Man-In-The-Middle-Attack (MiTM) happens when the transaction or communication between the intended recipients are intercepted by a third party. This type of attack is a form of eavesdropping, while the hacker tampers or extracts the sensitive information when exchanged by the two parties. Quoting an example from the olden times, Adam writes a letter to his girl friend, Evelyn, expressing his love for her, while an inquisitive postman, opens the letter to read and tweaks it to write something against her. Evelyn gets a bad opinion against Adam. Considering this case, the postman is the hacker here.
In today’s age, consider the same scenario, however its the hacker who sits in between the user and the browser, to capture and steal data that the user submits. The information could be sent through an email, or through a social media profile or even through individual’s search history. A MITM hacker can access the bank details of a user can be used to steal money.
Types of man-in-the-middle attacks:
Email Hijacking
Email Hijacking is done to either attack an individual or an organization along with other forms of attack methods like phishing and social engineering. Phishing is a type of attack, where hackers conceal their presence through mails as a genuine organization. Social engineering, on the other hand, helps hackers to understand the user’s activity to gain access to their confidential information. Once the email account is compromised, the communication between the two parties are monitored by the hackers and they try to get monetary benefits by stealing some user data from the hacked account.
Spoofing Attacks
The spoofing attacks, indulge the hackers to make a copy of the user’s programme to steal and extract data. In this case, the user will enter all the sensitive bank information on to the genuine-looking application, however, it’s not the original application he is accustomed to, it is the mere copy of a webpage created by the hacker to gain access to the user’s information. Spoofing attacks include IP addresses, ARP and DNS which can help hackers find a way to access the internal networks of the organization to extract data and also spread malicious software to the devices connected to the organization’s network.
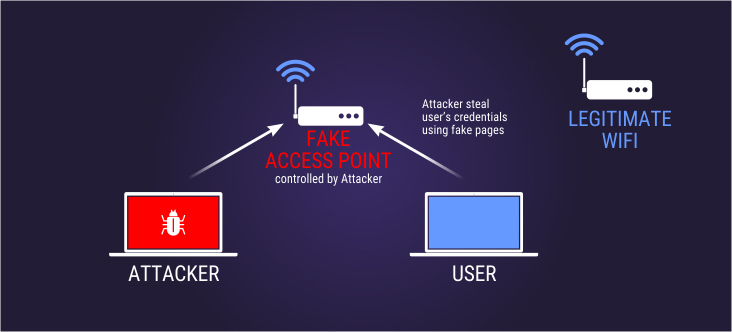
WiFi Hacking
It doesn’t matter, if you are using WPA2, WPA or WEP, however, hackers manage to creep in such wireless networks through Man-In-The-Middle-Attack. The hackers sniff the web traffic of the users by using caches and cookies to get into private accounts. They also create a Wi-Fi node that looks more like a secure Wi-Fi connection, that tricks the users to get connected to it. They also try and compromise the router by cracking its password. This is more likely to happen when the users connect their system to public Wi-Fi zones, which are mostly not secure.
How to protect my organizations from MITM attacks?
It is wise to use HTTPS protocol in any search engine browser as the HTTP protocol does not encrypt the information transmitted between the server and the browser. Also, the HTTP protocol does not detect MITM attacks and will not alert or notify the user. MiTM intercepts the communication between the intended recipients. Securing the communication channel is vital to keep the personal and professional information secure by keeping the hackers at bay.
Bring in the awareness to employees, that they should not access company’s sensitive data through public Wi-Fi networks. This comes as a first-line defense and it is much effective to protect the user’s and the company’s information as well.
Instilling the use of a certified authentication for all the privately owned devices; this denies malware entry through Wifi-networks, or internal networks or even through email systems.
Providing awareness and educating employees on how to go about data security and help them understand on what is identity theft and social engineering attacks would save the organizations from the crisis of security breaches and therefore a lot more than money.
Related Resources