August 6th, 2018 | By Administrator
Cybersecurity and Its Importance Cybersecurity refers to the processes, technologies, and practices that have been specially designed for protecting devices, programs, networks, and data from damage, unauthorized access, or attack. Cybersecurity is considered to be extremely...
MORE
June 14th, 2018 | By Administrator
In today’s increasingly connected and digital business environment, the incidence of zero-day attacks and consequences of data breaches are on the rise. Many well-known companies all over the world today have suffered from data breaches and zero-day attacks that have c...
MORE
May 11th, 2018 | By Administrator
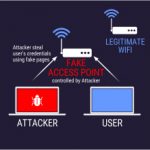
Cyber criminals find new ways, methods, and techniques to attack a user’s device or to even attack an organization’s network. One such type of attack is called Man in the Middle Attack. In this article, let’s discuss the Man-in-the-Middle Attacks. What is Man-In-The-Mi...
MORE