How to Protect your Organisation From Man in the Middle Attacks?
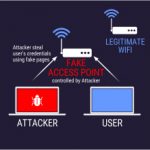
May 11th, 2018 | By AdministratorCyber criminals find new ways, methods, and techniques to attack a user’s device or to even attack an organization’s network. One such type of attack is called Man in the Middle Attack. In this article, let’s discuss the Man-in-the-Middle Attacks. What is Man-In-The-Mi...
MORE