As the name suggests, the man-in-the-middle attack is staged by a malicious user who secretly inserts him/herself between two communicating parties. So, when a hacker intercepts two unsuspecting parties he/she monitors the entire conversation and possibly tries to alter the data that is exchanged between each other. Mostly, the hacker impersonates to steal the data-in-transit.
Data knows no bounds – it keeps traveling from one system to another and from one region to another. Unluckily, security and privacy become a matter of grave concern only when data travels from one endpoint to another.
Apparently, the control over data-in-transit is fairly lost.
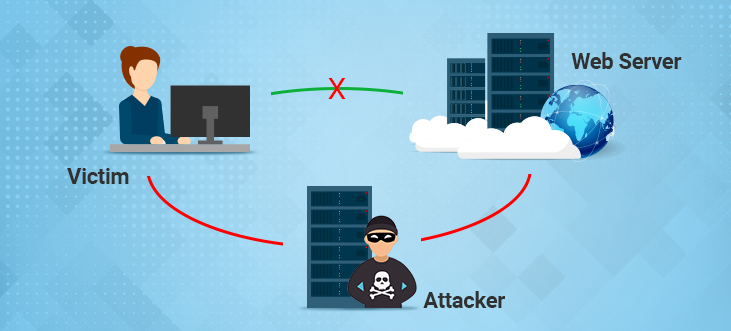
How does it work?
The attacker inserts into a conversation without revealing the identity to both endpoints, gains access to information by impersonating. Simply put, an attacker has the ability to intercept, send and receive information without the knowledge of the sender and receiver.
There are four ways of carrying out MITM attacks and they are Sniffing, SSL Stripping, Packet Injection, and Session Hijacking.
SSL Sniffing
Sniffing is also known as Packet Sniffing.
The hacker uses the SSL Sniffing technique to intercept and capture packets of data flowing in and out of a system or network. Many enterprises carry out packet sniffing for security reasons and it is legal to do so if employed correctly.
SSL Stripping
Secure Sockets Layer (SSL) Stripping also known as SSL Downgrade is the least used technique in MITM attacks. Usually, the job of the SSL/TLS certificates is to keep the online communication safe and secure via encryption. In the case of SSL Strip attacks, the traffic coming from the victim’s network is rerouted to the attacker’s proxy by stripping off the SSL/TLS connection.
Packet Injection
Packet Injection technique is normally used in denial-of-service attacks and man-in-the-middle attacks. Using this technique, a cybercriminal injects malicious packets of data into the regular data. The victim is made to believe that all files received are part of the legitimate communication stream. In many instances, the intrusion is undetected before its too late.
Session Hijacking
By making use of the Session Hijacking technique, an attacker tries to establish his/her presence in a session by intruding in real time. In this kind of attack, the hacker often targets potential discreet information. Depending on the nature of an attack, the intrusion may be detected or go undetected.
MITM Attack Prevention Strategies
It is vital to remember that man-in-the-middle attacks are complicated in nature. In order get rid of such online attacks from your system/network, you require the right set of tools and skilled personnel assistance.
Follow these best practices to stay protected against man-in-the-middle attacks
Never visit websites that have HTTP in front of the URL
Enable TLS 1.1 and TLS 1.2 if your website is using SSL and disable insecure SSL/TLS protocols
Never download pirated content
Never open suspicious links, files or emails – always verify their source
Install security tools on your system
Recommend your website admin to implement HSTS