April 13th, 2018 | By Administrator
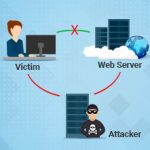
What is man-in-the-middle attack? As the name suggests, the man-in-the-middle attack is staged by a malicious user who secretly inserts him/herself between two communicating parties. So, when a hacker intercepts two unsuspecting parties he/she monitors the entire conversatio...
MORE
April 13th, 2018 | By Administrator
Establishing enterprise is one thing. Securing its dealings with outside world is another. The moment your enterprise goes online and interacts with others (be it client or third-party or other such intermediaries) the sensitive data which your enterprise holds becomes vulne...
MORE
April 4th, 2018 | By Administrator
Incidents of enterprises facing huge financial losses are not uncommon. And yet many of them usually ignore the flaws in their data security systems, hoping (or rather) praying that they might just be ignored by hackers. One of the major reasons for this behavior is that the...
MORE
March 27th, 2018 | By Administrator
The organizations are appalled with the elevated volume of breaches through the state of application exploits, malicious software, and botnets. Companies are high at risk due to higher rate of threats while they perform online operations. It is therefore vital to understand...
MORE
March 21st, 2018 | By Administrator
The use of the internet is ever-present at the current hour, the immense reliability on the Internet as a medium to carry out financial or personal transaction makes it prone to attacks. A bevy of cyber thieves is hooked on with an extra pair of glasses to gain access to sen...
MORE
March 16th, 2018 | By Administrator
It’s a well-known fact that POS (Point Of Sale) systems are vulnerable to security attacks. So if POS systems are not protected well using the right kind of security tools, enterprises which employ them, and above all, the data present within those POS systems will be...
MORE
March 1st, 2018 | By Administrator
Since Jan 3, Meltdown and Specter attack has been in the news and it all takes shape from hardware security vulnerability. So chips from Intel, AMD, and ARM have a vulnerable hole. This is according to Anders Fogh the German cyber website Information was first made available...
MORE
February 20th, 2018 | By Administrator
The year 2018 started on a sober note with ATM jackpotting hitting the US cities. The Secret Service came into action after the reports came about jackpotting, that lets anyone steal money from ATMs. Well, this was something new that has happened in the United States, where...
MORE
January 28th, 2018 | By Administrator
Retail industry and security breaches are inseparable. A single attack can compromise millions of identities. The intensity and sophisticated nature of cyber attacks are posing huge problems for businesses who hold the responsibility of protecting their customers’ pers...
MORE
January 26th, 2018 | By Administrator
For financial organizations across the world, 2017 proved to be eventful. There were all kinds of cyber security incidents- malware strikes, credit card breaches, ATM attacks, hijacking bank domains to intercept customers’ electronic operations etc. 2017 saw the first...
MORE