May 4th, 2019 | By Administrator
Distributed Denial of Service in short is commonly called DDoS. This is a type of cyberattack that weaves in a combination of sophisticated and dynamic attack methods to evade internet-facing devices. It attempts to load the normal traffic of the victim server or business ne...
MORE
February 21st, 2019 | By Administrator
With organizations and companies offering more online services and transactions, internet security is indeed becoming an essential necessity and also a priority in order to guarantee the safety of all sensitive information that gets transferred to legitimate online businesse...
MORE
August 6th, 2018 | By Administrator
Cybersecurity and Its Importance Cybersecurity refers to the processes, technologies, and practices that have been specially designed for protecting devices, programs, networks, and data from damage, unauthorized access, or attack. Cybersecurity is considered to be extremely...
MORE
May 11th, 2018 | By Administrator
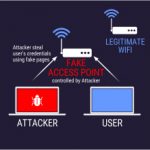
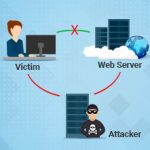
Cyber criminals find new ways, methods, and techniques to attack a user’s device or to even attack an organization’s network. One such type of attack is called Man in the Middle Attack. In this article, let’s discuss the Man-in-the-Middle Attacks. What is Man-In-The-Mi...
MORE
April 13th, 2018 | By Administrator
What is man-in-the-middle attack? As the name suggests, the man-in-the-middle attack is staged by a malicious user who secretly inserts him/herself between two communicating parties. So, when a hacker intercepts two unsuspecting parties he/she monitors the entire conversatio...
MORE
April 13th, 2018 | By Administrator
Establishing enterprise is one thing. Securing its dealings with outside world is another. The moment your enterprise goes online and interacts with others (be it client or third-party or other such intermediaries) the sensitive data which your enterprise holds becomes vulne...
MORE
March 21st, 2018 | By Administrator
The use of the internet is ever-present at the current hour, the immense reliability on the Internet as a medium to carry out financial or personal transaction makes it prone to attacks. A bevy of cyber thieves is hooked on with an extra pair of glasses to gain access to sen...
MORE
February 13th, 2017 | By Administrator
It was almost a year ago, late in February 2005, that laptops from PC maker Lenovo that were shipped were found to be installed with adware called “Superfish”. Following this incident, Facebook investigated the issue of SSL-sniffing software being packaged as see...
MORE
June 20th, 2016 | By Administrator
SSL certificates are now increasingly used to secure websites and prevent theft of sensitive personal data. The tech-savvy may very well know what SSL certificates are, but for non-technical people SSL certificates may seem rather unfamiliar. What’s SSL Certificate? SS...
MORE