May 17th, 2019 | By SEO India
Enterprise Security Solution: Introduction More and more people are now relying on cloud-based technologies. Most of us upload and save their files on the cloud every now and then. Some companies still rely on their existing equipment. This scenario poses some risks. An ente...
MORE
May 13th, 2019 | By Administrator
Data is a critical resource for businesses of any size; it is therefore vital to strengthen data security. Data is transferred across multiple channels through the internet and becomes vulnerable to online data breaches. Data Security is critical to ensure protection of impo...
MORE
April 13th, 2018 | By Administrator
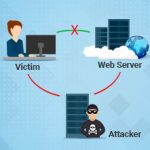
What is man-in-the-middle attack? As the name suggests, the man-in-the-middle attack is staged by a malicious user who secretly inserts him/herself between two communicating parties. So, when a hacker intercepts two unsuspecting parties he/she monitors the entire conversatio...
MORE
April 13th, 2018 | By Administrator
Establishing enterprise is one thing. Securing its dealings with outside world is another. The moment your enterprise goes online and interacts with others (be it client or third-party or other such intermediaries) the sensitive data which your enterprise holds becomes vulne...
MORE
January 27th, 2017 | By Administrator
Reports came up recently stating that several states across the US have started reviewing cyber security as regards critical infrastructure following reports that a laptop at the Burlington Electric Department was found to be infected with malware. Reports indicated that the...
MORE